Home » What Are HTTP, HTTPS & SOCKS5 Proxies – and Why You Should Use Them
What Are HTTP, HTTPS & SOCKS5 Proxies - and Why You Should Use Them
- Author: George Fellow
- Date Posted: July 4th, 2024
- Category: Proxy Companies
Proxy protocols have evolved significantly over the past few decades, adapting to the increasing demands for security, speed, and anonymity in web browsing and data exchange. Understanding these protocols is essential for anyone in the proxy industry, as each type offers distinct advantages and is suited to different use cases. This article traces the development of proxy protocols from HTTP to SOCKS5 and beyond, providing a detailed overview of their functionalities, benefits, and specific applications.
HTTP Proxies
Overview of HTTP Proxies
HTTP proxies were among the first widely adopted proxy protocols. They function primarily as intermediaries between a client and a server for web traffic, specifically designed to handle HTTP requests. When a client makes a request to access a web page, the HTTP proxy forwards this request to the server, receives the response, and then sends it back to the client. These proxies manage data flow between users and the internet, masking the user’s IP address and providing anonymity.
HTTP proxies offer additional functionalities, including traffic filtering and load balancing, which help manage network traffic more efficiently. As an intermediary, HTTP proxies can facilitate various functions, such as hiding the user’s IP address, thereby providing anonymity. They can also cache web content, which helps reduce latency and bandwidth usage for frequently accessed resources, making them essential for speeding up access to commonly visited websites.
Advantages of HTTP Proxies
HTTP proxies offer several benefits, particularly in web browsing scenarios. They are easy to configure and provide essential anonymity by hiding the client’s IP address. Additionally, HTTP proxies can cache web content, reducing latency and bandwidth usage for frequently accessed resources, improving load times, and reducing server load. This simplicity contributes to their widespread adoption and easy integration into most web browsers and systems.
HTTP proxies enhance the browsing experience by improving load times and reducing server load through caching. They are instrumental in scenarios where quick access to frequently visited websites is crucial. The ability to filter traffic and balance loads makes HTTP proxies invaluable for managing network efficiency and ensuring smooth internet operations.
Use Cases of HTTP Proxies
HTTP proxies are well-suited for content filtering and web scraping. Businesses use them to restrict access to specific websites and monitor employee web activity. Meanwhile, web scraping enthusiasts leverage HTTP proxies to gather data from various websites without getting blocked. Services like ScraperAPI, Bright Data offer robust HTTP proxy solutions that support large-scale data extraction tasks, making them ideal for these purposes.
HTTP proxies enforce internet usage policies. Schools and companies use these proxies to block access to inappropriate or non-productive websites, ensuring a focused and safe browsing environment. This capability is essential for maintaining productivity and security within these environments, highlighting the versatility and importance of HTTP proxies in various applications.
Advancements with HTTPS Proxies
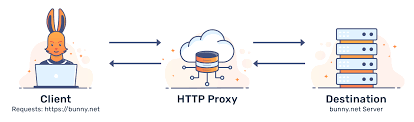
Introduction of HTTPS Proxies
As the need for secure web communications grew, HTTPS proxies emerged. These proxies support the SSL and TLS protocols, enabling encrypted communication between the client and the server. HTTPS proxies ensure that sensitive data, such as login credentials and financial information, is securely transmitted. This development marked a significant step forward in enhancing online security.
The development of HTTPS proxies addressed the growing demand for secure and confidential online communications. By encrypting data, these proxies prevent unauthorized access and interception, making them essential for protecting personal and corporate information. HTTPS proxies have thus become a standard in industries where confidentiality and data integrity are paramount.
Advantages of HTTPS Proxies
The primary advantage of HTTPS proxies is their ability to provide a secure browsing experience. By encrypting data, they protect against eavesdropping and man-in-the-middle attacks, maintaining the caching benefits of their HTTP counterparts while ensuring both speed and security. This dual advantage makes HTTPS proxies highly valuable in scenarios where both performance and data security are critical.
Moreover, HTTPS proxies support a wide range of online activities that require a high level of security. From online banking to confidential communications, these proxies protect all data transactions. They also help maintain compliance with various data protection regulations, which are increasingly important in today’s digital market.
Use Cases of HTTPS Proxies
HTTPS proxies are indispensable for accessing secure websites and conducting financial transactions online. Businesses commonly use them to secure their internal communications and protect customer data. Furthermore, HTTPS proxies bypass geo-restrictions, enabling users to securely access content from different regions. Providers like Oxylabs and Smartproxy offer HTTPS proxies with high-security standards, ensuring safe and anonymous browsing.
These proxies are also critical for personal use where privacy is a concern. Individuals who need to access sensitive accounts or conduct private transactions can benefit from the enhanced security of HTTPS proxies. Additionally, they are helpful for circumventing government censorship, allowing users to access blocked websites safely and privately.
The Flexibility of SOCKS Proxies
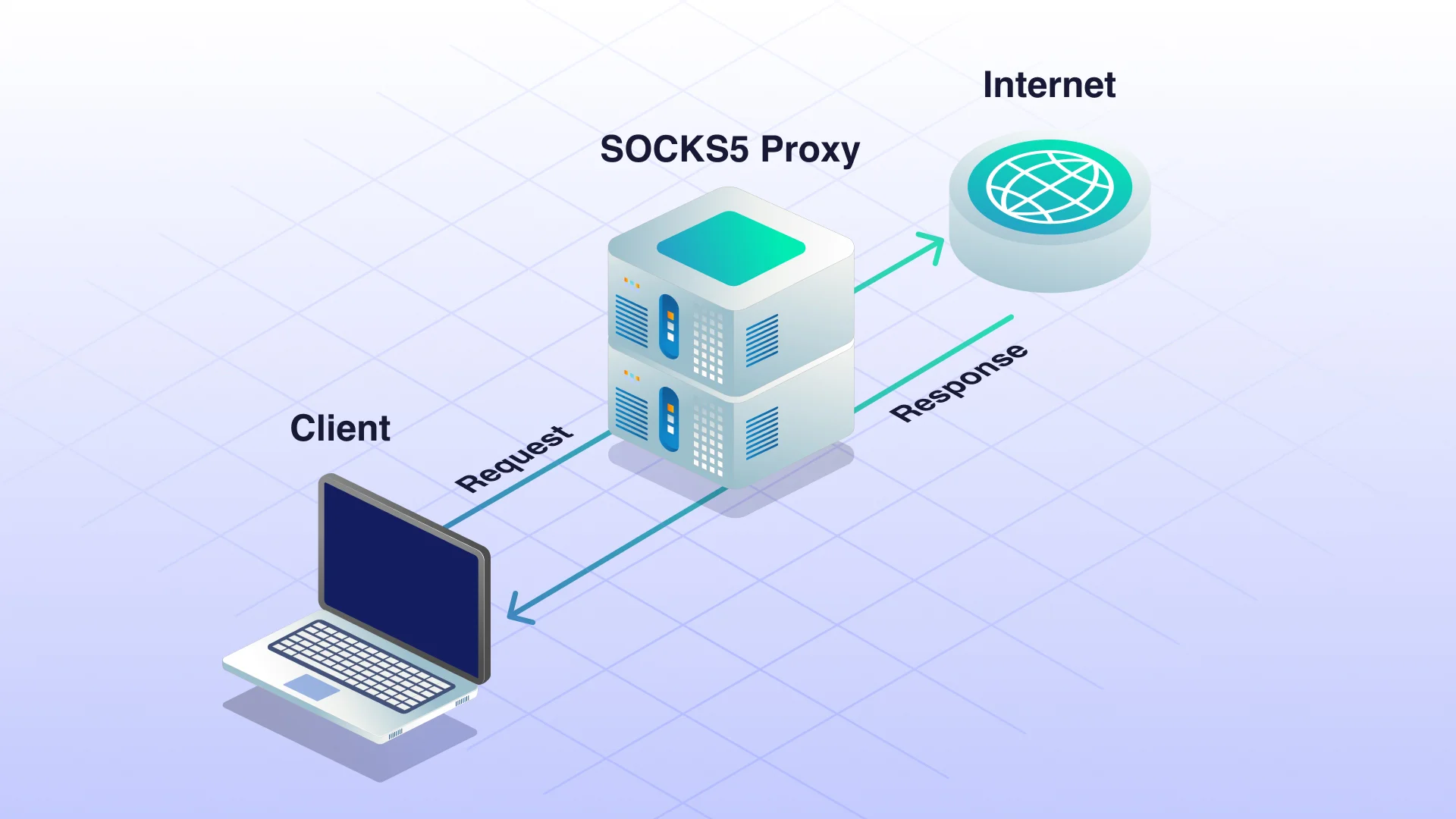
Emergence of SOCKS Proxies
SOCKS proxies marked a significant advancement in proxy technology. Unlike HTTP and HTTPS proxies that operate at the application layer, SOCKS proxies function at the transport layer, allowing them to handle a broader range of traffic types, including HTTP, HTTPS, FTP, and even email protocols. This capability makes SOCKS proxies extraordinarily versatile and suitable for more complex networking tasks.
Operating at the transport layer allows SOCKS proxies to support Internet protocols beyond web traffic. This versatility makes them suitable for tasks that require handling different data types, such as real-time applications and complex networking setups. As a result, SOCKS proxies have become an essential tool in modern internet communication.
Advantages of SOCKS Proxies
SOCKS proxies offer greater flexibility and performance. They are protocol-agnostic, meaning they can forward any traffic. This versatility makes them suitable for applications beyond web browsing, such as handling UDP traffic for real-time gaming and video streaming applications. The ability to handle different types of network requests efficiently enhances their utility in diverse scenarios.
The support for UDP traffic is particularly beneficial for applications requiring fast and efficient data transfer. Online games and VoIP services benefit from the low latency and high speed provided by SOCKS proxies, making them a preferred choice for users needing a reliable and swift connection. This flexibility ensures that SOCKS proxies can meet the demands of various modern internet activities.
Use Cases of SOCKS Proxies
SOCKS proxies are particularly popular for activities requiring high levels of anonymity and versatility. They are used in torrenting to mask the user’s IP address and enhance privacy. Gamers leverage SOCKS proxies to reduce latency and improve their gaming experience. Additionally, SOCKS proxies are favored for bypassing internet censorship and accessing restricted content. Services like IPVanish and NordVPN offer robust SOCKS5 proxy solutions for these use cases.
These proxies are also utilized in professional environments where secure and efficient data transfer is crucial. Businesses that rely on FTP to transfer large files can use SOCKS proxies to ensure these transfers are fast and secure. This makes SOCKS proxies essential for many IT operations and enterprise-level applications.
The Rise of SOCKS5 Proxies

Introduction of SOCKS5 Proxies
SOCKS5 is an enhanced version of the SOCKS protocol, offering additional features such as authentication and support for IPv6. SOCKS5 proxies provide higher security and efficiency, making them a preferred choice for many advanced proxy users. Including authentication methods ensures only authorized users can access the proxy server, significantly enhancing security.
The introduction of support for TCP and UDP traffic in SOCKS5 allows it to handle a broader range of Internet applications. This feature, combined with IPv6 compatibility, ensures that SOCKS5 proxies can meet the evolving needs of internet users and remain relevant in the changing digital world.
Advantages of SOCKS5 Proxies
The key advantages of SOCKS5 proxies include their support for authentication, which allows only authorized users to access the proxy server. SOCKS5 also supports TCP and UDP traffic, providing robust application performance. Including IPv6 support ensures compatibility with the latest internet technologies, making SOCKS5 proxies highly adaptable and future-proof.
SOCKS5 proxies offer improved performance and reliability. They can handle higher traffic volumes and provide faster connection speeds, making them suitable for personal and professional use. The enhanced security measures also make them ideal for applications where data protection is critical.
Use Cases of SOCKS5 Proxies
SOCKS5 proxies are extensively used for secure and anonymous web browsing, especially in environments requiring enhanced security. They are also favored in the cybersecurity industry for penetration testing and vulnerability assessments. Moreover, SOCKS5 proxies are utilized in complex networking setups, including VPNs (Virtual Private Networks) and secure corporate networks. Providers like TorGuard and Private Internet Access offer reliable SOCKS5 proxy services for these advanced needs.
SOCKS5 proxies also find applications in digital marketing and SEO tasks, where they help manage multiple social media accounts and gather competitive intelligence. Their robustness and reliability make them suitable for various professional needs, including managing complex networking setups and ensuring secure connections for remote workers. This versatility makes SOCKS5 proxies a valuable tool for many industries.
Comparative Analysis: SOCKS5 vs. HTTP Proxies
When comparing SOCKS5 and HTTP proxies, SOCKS5 offers greater versatility and security. While HTTP proxies are limited to web traffic, SOCKS5 can handle a variety of protocols, including FTP, SMTP, and more. Additionally, the authentication feature in SOCKS5 enhances security, making it a better choice for sensitive applications. However, HTTP proxies are more straightforward to configure and may be sufficient for basic web browsing needs.
The choice between SOCKS5 and HTTP proxies ultimately depends on the user’s specific requirements. For tasks that require handling multiple types of internet traffic and ensuring high security, SOCKS5 proxies are the better option. On the other hand, for straightforward web browsing and simple tasks, HTTP proxies provide a more accessible and easier-to-implement solution. Understanding the strengths and limitations of each type can help users select the appropriate proxy for their needs.
Beyond SOCKS5: Emerging Proxy Protocols
Innovations in Proxy Technology
As internet usage continues to evolve, new proxy protocols and enhancements are being developed to address emerging challenges. Innovations such as Multipath TCP and QUIC pave the way for faster and more reliable internet connections. These technologies aim to optimize data transfer by utilizing multiple paths and improving congestion control, enhancing the overall internet experience.
These emerging protocols are designed to meet the growing demands for high-speed and low-latency connections. By leveraging advanced networking techniques, they can significantly improve performance and reliability. This makes them particularly suitable for applications that require real-time data transmission, such as online gaming, live streaming, and video conferencing.
Advantages of Emerging Proxy Protocols
Emerging proxy protocols offer significant improvements in speed, reliability, and security. MPTCP allows simultaneous use of multiple network interfaces, enhancing redundancy and performance. QUIC, on the other hand, is designed to reduce latency and improve connection reliability, making it ideal for real-time applications where quick and stable connections are crucial.
The ability to use multiple paths for data transfer in MPTCP increases the robustness of connections, ensuring that data can be rerouted in case of a failure in one of the paths. This enhances the overall reliability and efficiency of the network. QUIC’s focus on reducing latency makes it highly effective for applications where speed and responsiveness are essential.
Future Trends: Proxy Protocols in the Next Decade
Integrating AI (Artificial Intelligence) and ML (Machine Learning) with proxy protocols is a promising trend. AI can optimize proxy usage by dynamically adjusting configurations based on traffic patterns and user behavior, leading to more efficient and secure data routing. This can significantly enhance the performance and security of internet connections.
Additionally, advancements in quantum computing may introduce new proxy protocols that leverage quantum encryption for unparalleled security. Quantum encryption can provide a level of security currently unattainable with traditional encryption methods, protecting data against even the most sophisticated cyber threats. This combination of AI and quantum computing represents a significant step forward in the evolution of proxy protocols.
Security Considerations in Proxy Protocols

Understanding Proxy Vulnerabilities
While proxy protocols offer numerous benefits, they are not without their vulnerabilities. Each type of proxy has its own set of potential security risks. For example, while easy to use, HTTP proxies can be susceptible to man-in-the-middle attacks if not properly secured. Despite their encryption, HTTPS proxies can be targeted by SSL stripping attacks if users are not vigilant.
Understanding these vulnerabilities is crucial for anyone using proxy services. By being aware of the potential risks, users can take steps to mitigate them and ensure their data remains secure. Regular updates and proper configuration of proxy servers are essential to maintaining security and protecting against potential threats.
Mitigating Risks with Proper Configuration
Proper configuration and management of proxy servers are crucial to mitigating these risks. Regular updates, robust authentication methods, and additional security measures such as firewalls and intrusion detection systems can significantly enhance the security of proxy servers. Moreover, educating users about safe proxy practices is essential to prevent common pitfalls and ensure a secure browsing experience.
Ensuring that proxy servers are configured correctly involves establishing strong access controls and monitoring network traffic for suspicious activity. Using encryption for all communications and implementing multi-factor authentication can further protect against unauthorized access. Regular security audits and updates are also necessary to keep the proxy servers secure against new threats.
Industry Best Practices for Proxy Security
Adopting industry best practices is critical to ensuring the security and reliability of proxy servers. These practices include implementing strict access controls, regularly auditing proxy logs, and using secure and reputable proxy providers. Employing multi-factor authentication (MFA) and encrypting all communications can further safeguard against potential threats.
By following these best practices, organizations can significantly reduce the risk of security breaches and ensure their proxy servers remain secure. Using reputable proxy providers is also essential, as they typically offer better security features and support. Regular training and awareness programs for users can help maintain a high level of security within the organization.
User Experiences and Reviews
User Testimonials
Many professionals in various fields have shared positive experiences with using proxies. For instance, digital marketers often use proxies to manage multiple social media accounts and perform competitive analysis. They report significant improvements in efficiency and effectiveness by using proxies to bypass restrictions and automate tasks. Proxies have also benefited researchers who need to gather data from different geographic locations. By using proxies, they can simulate access from various regions, providing a more comprehensive view of global data trends.
Proxies have become essential for businesses looking to expand their market reach and understand international consumer behavior. By leveraging proxies, companies can gather data from different regions without facing IP bans or restrictions. This capability is handy for market researchers and analysts requiring accurate and comprehensive data.
Reviews of Popular Proxy Services
Several proxy service providers have garnered praise for their reliable and high-performance offerings. Users frequently highlight the ease of use, speed, and customer support as critical factors in their satisfaction. Reviews of services like Bright Data, Smartproxy, and Oxylabs reflect their reputation for providing robust and secure proxy solutions. These providers have built strong reputations by consistently delivering high-quality services.
The positive reviews from satisfied customers underscore the importance of choosing a reputable proxy provider. These providers offer excellent performance and reliability, which are critical for users who rely on them for business and personal use. Their commitment to security and customer satisfaction has made them leaders in the proxy industry.
In-Depth Provider Profiles
ScraperAPI
ScraperAPI specializes in web scraping solutions, offering powerful HTTP proxies that can handle large-scale data extraction tasks. Their proxies are optimized for speed and reliability, making them ideal for businesses needing to scrape massive amounts of data without getting blocked. The service also provides tools and features that simplify the web scraping process, including automatic IP rotation and user-agent management.
These capabilities help users gather data efficiently while minimizing the risk of being detected or blocked by target websites. ScraperAPI’s focus on web scraping makes it a valuable tool for market researchers and data analysts who require extensive and reliable data collection.
Bright Data
Bright Data offers many proxy types, including HTTPS and SOCKS. They are known for their extensive network and high-security standards, making them a top choice for businesses needing versatile and secure proxy solutions. The company provides proxies that cater to various use cases, from web scraping to ad verification and market research. Their network includes millions of IP addresses worldwide, ensuring high availability and performance.
Bright Data’s commitment to security and compliance makes it a reliable partner for businesses operating in sensitive industries. Their proxies offer excellent performance and reliability, which are critical for users who rely on them for business and personal use for their business and personal needs. Their comprehensive network ensures users can access a wide range of IP addresses, enhancing the effectiveness of their proxy solutions.
Oxylabs
Oxylabs is renowned for its high-security HTTPS proxies. They provide solutions that cater to businesses requiring secure access to web resources, including financial institutions and large enterprises. Their proxies ensure data integrity and confidentiality, making them a trusted provider in the industry. In addition to their HTTPS proxies, Oxylabs offers residential and datacenter proxies that can handle large volumes of traffic.
Oxylabs’ services are designed to meet the needs of demanding applications, such as data collection and analysis. Their focus on security and performance makes them a preferred choice for organizations prioritizing data protection. This commitment to high service standards has earned them a strong reputation among their clients.
Smartproxy
Smartproxy offers versatile proxy solutions for various applications, including web scraping, ad verification, and market research. Their proxies are known for their ease of use and high performance, making them popular among digital marketers and researchers. The company provides a range of proxy types, including residential and data center proxies, to meet different needs.
Smartproxy’s user-friendly platform and excellent customer support make it easy for users to set up and manage their proxies. Their commitment to delivering high-quality services has earned them a strong reputation in the industry. This reliability and versatility make Smartproxy a valuable tool for various online activities.
IPVanish
IPVanish provides robust SOCKS5 proxies that are particularly well-suited for torrenting and gaming. Their proxies offer low latency and high speeds, ensuring a seamless experience for users needing reliable and fast connections. The service also offers advanced features such as unlimited bandwidth and access to over 1,500 servers worldwide.
These features make IPVanish an excellent choice for users who require high-performance proxies for demanding applications. The company’s focus on privacy and security ensures users enjoy a safe and anonymous online experience. This dedication to quality makes IPVanish a trusted name in the proxy industry.
Coronium.io
Coronium.io is a relatively new player in the proxy market but has quickly established itself as a reliable provider. Specializing in mobile proxies, Coronium.io focuses on providing high-speed and secure connections for mobile devices. Their services are tailored to meet the needs of both individuals and businesses, ensuring versatility and performance.
One of Coronium.io‘s standout features is its user-friendly dashboard, which makes managing proxies straightforward, even for those new to the field. Additionally, they offer 24/7 customer support and flexible pricing plans, making their services accessible to many users. Their commitment to innovation and customer satisfaction has helped them build a solid reputation in a competitive market.
Conclusion
The evolution of proxy protocols from HTTP to SOCKS5 and beyond highlights the continuous advancements in Internet technology. Each protocol offers unique advantages and is tailored to specific use cases, catering to the diverse needs of modern internet users. As new challenges and requirements emerge, the development of innovative proxy protocols will continue to shape the future of secure, efficient, and anonymous Internet usage.
Proxy services have become integral to various online activities, from web scraping and content filtering to secure browsing and data protection. Understanding the evolution of these protocols allows users to make informed decisions about the best proxy solutions for their specific needs. As the proxy industry advances, staying updated with the latest developments will ensure optimal performance and security in an ever-changing digital market.
Choosing the exemplary proxy service is crucial for achieving optimal performance and security. By understanding the strengths and applications of different proxy protocols, users can navigate the proxy landscape with confidence and efficiency.
